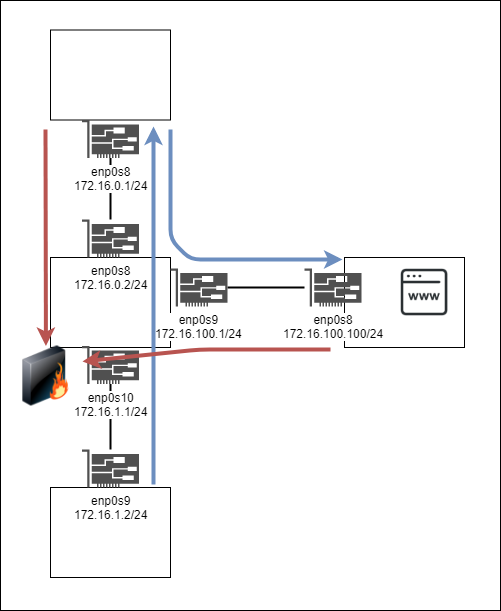
# firewall-cmd --list-all --zone=external
external (active)
target: default
icmp-block-inversion: no
interfaces: enp0s8
sources:
services:
ports:
protocols:
masquerade: yes
forward-ports: port=80:proto=tcp:toport=80:toaddr=172.16.100.100
source-ports:
icmp-blocks:
rich rules:
# firewall-cmd --list-all --zone=block
block (active)
target: %%REJECT%%
icmp-block-inversion: no
interfaces: enp0s9
sources:
services:
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
# firewall-cmd --list-all --zone=internal
internal (active)
target: default
icmp-block-inversion: no
interfaces: enp0s10
sources:
services: ssh mdns samba-client dhcpv6-client
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
activeゾーンの確認
# firewall-cmd --get-active-zone
ゾーンにNICを割り当てる
# firewall-cmd --add-interface=enp0s9 --zone=block --permanent
firewallの状態確認
# firewall-cmd --list-all --zone=block
portforwardの追加/削除
# firewall-cmd --add-forward-port=port=80:proto=tcp:toport=80:toaddr=172.16.100.100 --zone=external --permanent
# firewall-cmd --remove-forward-port=port=80:proto=tcp:toport=80:toaddr=172.16.100.100 --zone=external --permanent
firewallを通過できるサービスの追加/削除
# firewall-cmd --add-service=ssh --permanent
# firewall-cmd --remove-service=ssh --permanent
firewallを通過できるポートの追加/削除
# firewall-cmd --add-port=80/TCP --permanent
# firewall-cmd --remove-port=80/TCP --permanent